There is lots of talk the past few hours about how the FBI seized bitcoins extorted by Darkside from Colonial Pipeline during the ransomware cyberattack they launched on the oil pipeline. Unfortunately, the news is also being dished out with a large side order of misinformation. People are starting to think that the FBI hacked bitcoin or hacked the private keys for the Darkside address. Now investors are selling like crazy causing the BTC price to slump again.
For some reason, people are also claiming that the FBI served Coinbase with a seizure warrant, even though there’s no evidence of the bitcoins being stored on Coinbase in the first place.
So while all this was going on, I decided to trace the stolen Bitcoins myself, using nothing more than my trusty tools, Blockchair and Wallet Explorer. They are both free to use, so you are able to reproduce these results as well if you want. Now on to the investigation.
Zoning in on the ransom transaction
News media was frustratingly vague about which transactions and addresses were involved in the heist, but a reference from one of these news articles, a report by Elliptic stated that 75 BTC were transferred by Colonial Pipeline to the hacker’s wallet address on May 8.
“This wallet received the 75 BTC payment (worth $4.4 million at the time of the transaction) made by Colonial Pipeline on May 8, following the crippling cyberattack on its operations – leading to widespread fuel shortages in the US.”
Dr. Tom Robinson, Co-founder of Elliptic
They did not mention what was the wallet address of the hackers. But to find it, I just had to put a few pieces of information together:
- The transaction had a 75 BTC output, and it happened on May 8
- It’s safe to assume that Colonial Pipeline has almost no knowledge of bitcoin, so they bought the 75BTC from an exchange. Exchanges send user transactions in 1-input, 2-output format.
- The second output would be to a change address (the remainder of the money from the input that wasn’t spent) but in this case, it would be extremely small as the input and first output are almost the same size.
Armed with this information, I opened Blockchair, headed towards the Transactions category, and then used their filters to give me only the transactions with a total output size between 74 and 76 BTC, and occurring on May 8. I knew that only 1-input and 2-input transactions were relevant. Here is the resulting Blockchair query.
There were not many transactions returned from this result, only about 30 or so. But only one of them precisely matched what I was looking for. It was transaction fc78327d4e46dac01dc313067b1ac7f274cdb3a07ea9f28f6f71473145f1b264. I was starting to get a lead.
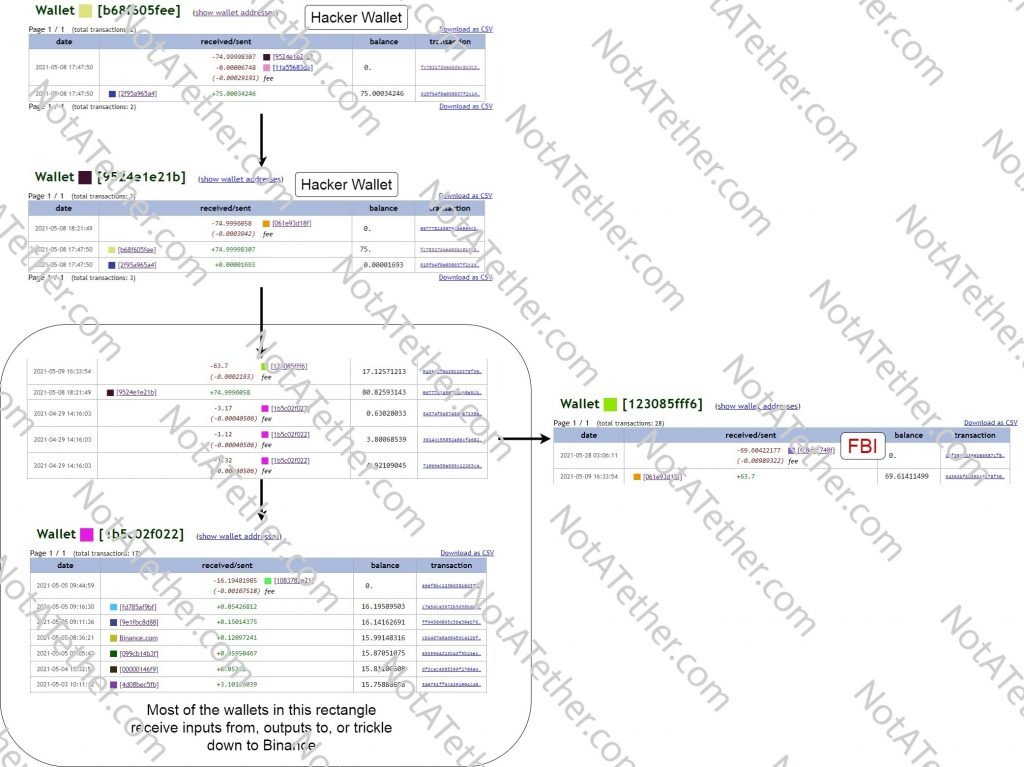
All further investigation would be carried out at Wallet Explorer. Pasting the above transaction ID into it gave me the wallet [b68f605feedee27e], associated with address 1DToN8Q6y31TGAz75Df729Bnujk6Xg7q5X. Then the 75 BTC was transferred to wallet [9524e1e21b] of address bc1q7eqww9dmm9p48hx5yz5gcvmncu65w43wfytpsf, then to [061e93d18f]. What’s interesting about wallet [061e93d18f] is that it has received a few dozen previous transactions before this incident, and some more since then.
Hacker’s wallet, or an exchange?
Was this a software wallet which may have just received ransomware payments from others, or was it something deeper? Could it be the entry point to an exchange?
As you might know, exchanges make heavy use of deposit and withdrawal addresses. It is not uncommon to see these addresses having thousands of pages of transaction history. Also present in an exchange’s architecture are cold storage addresses – these addresses collect the balances of the deposit addresses into their own.
It could have also been a payment processor address. Many news sites have reported that Darkside was using a payment processor to collect the ransoms, and a payment processor generates a different address for each payment. Typically, these different payment addresses are then “feeded” into a main address. This is what seems to be happening here: bc1q7eqww9dmm9p48hx5yz5gcvmncu65w43wfytpsf belongs to payment processor “deposit address” wallet [9524e1e21b], and both of the addresses bc1qxu83k5qkj8kcqdqqenwzn7khcw4llfykeqwg45 and bc1qu57hnxf0c65fsdd5kewcsfeag6sljgfhz99zwt belong to the main wallet [061e93d18f]. These two addresses have split the 75 BTC into about 63.7 BTC and 11.2 BTC respectively.
11.2/75 roughly equals 0.15, so one explanation for this divide could be that profit sharing is going on here. DarkSide may have received a 15% cut of the ransomware payment (which closely aligns with previous claims that they take 25% of the cut from its affiliates), which means bc1qu57hnxf0c65fsdd5kewcsfeag6sljgfhz99zwt is a DarkSide address. While the remaining 85% of the BTC was taken by the affiliate to address bc1qxu83k5qkj8kcqdqqenwzn7khcw4llfykeqwg45.
The affiliates address contains a particular transaction 9436dbf0435b15378f309c35754a110db880fa9bb66a062160a25533bb4a212a to address 3EYkxQSUv2KcuRTnHQA8tNuG7S2pKcdNxB, part of the [123085fff6] wallet.
This is an address that begins with 3, or a P2SH address. It is not particularly simple to create a P2SH in offline wallets. Assuming the affiliate did not have advanced knowledge about bitcoin, the likely possibility is that the payment processor deposited the 63.7 BTC onto an exchange address.
For the next stage of analysis, we must inspect the receiving wallets from the [123085fff6] wallet.
Three wallets this wallet has send bitcoins to at approximately the same timeframe are [149d0ee75d], [07a4235953], and [07a4235953]. Following the trail of each of these addresses, we end up at a high-transaction volume address each time. Curiously, each of those addresses has received at least one 1-input transaction from a known Binance address. [149d0ee75d] is an obvious example of this.
So my theory is the affiliate gave his Binance deposit address to the Darkside group for payments to it. But why would the affilate do that, when it is well known that exchanges are insecure places to hold large sums of money? Could it be that the affiliate wanted to cash out some of it?
The FBI seizure
It is well-agreed on that the FBI sent a warrant to an exchange to seize the 63.7 BTC, in other words, the affiliate’s bitcoins. The above investigation suggests that Binance was the receipent of such a warrant. It would not be possible to send a warrant to independent wallet developers such as Electrum or Bitcoin Core, who have no control over their user’s money. This gives more credibility to the claim that the affiliate stored his bitcoins on an exchange.
Wallet Explorer shows that the entire balance of the [123085fff6] wallet was sent to the [fc8d1c748f] wallet on 2021-05-28 03:06:11. This wallet might have links to the FBI, but how to prove it?
The FBI has claimed multiple times in a court document that they possess the private key to the address containing the stolen bitcoins. However, it is extremely unlikely that they obtained it from Binance, or managed to retrieve the private keys to Binance’s cold storage. That is because exchanges do not make addresses for each wallet user for efficiency reasons, and they lump together everyone’s balance in cold storage such as a hardware wallet. Therefore, it is plausible to believe that the [fc8d1c748f] wallet was already owned by the FBI, and that they just demanded Binance to send the affiliate’s stolen 63.7 BTC to it.
Curiously, people have suggested that Coinbase received the FBI warrant. However, there is no blockchain evidence that shows Coinbase addresses were involved. Also interesting is that the funds in the [fc8d1c748f] wallet have moved since the court document was published two days ago. Perhaps the FBI didn’t want us to snoop on their seized bitcoins?
Unrelated to all this, it seems that almost the entire balance of the Darkside group was stolen from them on May 13 by an unknown actor, with a transaction from Darkside’s [061e93d18f] wallet to bc1q2sewgrnau4e4gvceh8ykzf8lqxawpluu0k0607 shifting more than 107 bitcoins from them.
I have created a graph of the transactions flowing between Darkside , the affiliate’s wallet on Binance, and the FBI is below, minus the theft transaction from Darkside’s wallet (full size).
But did they hack bitcoin to get them?
Of course not. Here are some reasons why hacking bitcoin is still not feasible in 2021, and probably never will be in the near future:
- The ECDSA algorithm which mangles public and priavte keys into signatures for transactions still hasn’t witnessed a single breach. The FBI could not have hacked ECDSA.
- Second, the fastest tools for brute forcing private keys can only find 2^60 of them in a reasonable time, well below the number of bitcoin private keys, 2^256.
- Third, the bitcoins weren’t even seized from a private wallet, they were seized from an exchange who legally agreed to hand the bitcoins over via a transaction.
Most importantly, we now know that the stolen bitcoins were on an exchange. This proves rumors that the FBI hacked Darkside’s servers to be false. The closing of their website and servers was the result of their service provider terminating their access for law enforcement reasons, and the theft of nearly all of Darkside’s bitcoin, including the 11.2 BTC from the Colonial Pipeline ransom, was done by an unknown assailant, unrelated to the affiliate’s 63.7 BTC seized by the FBI.

